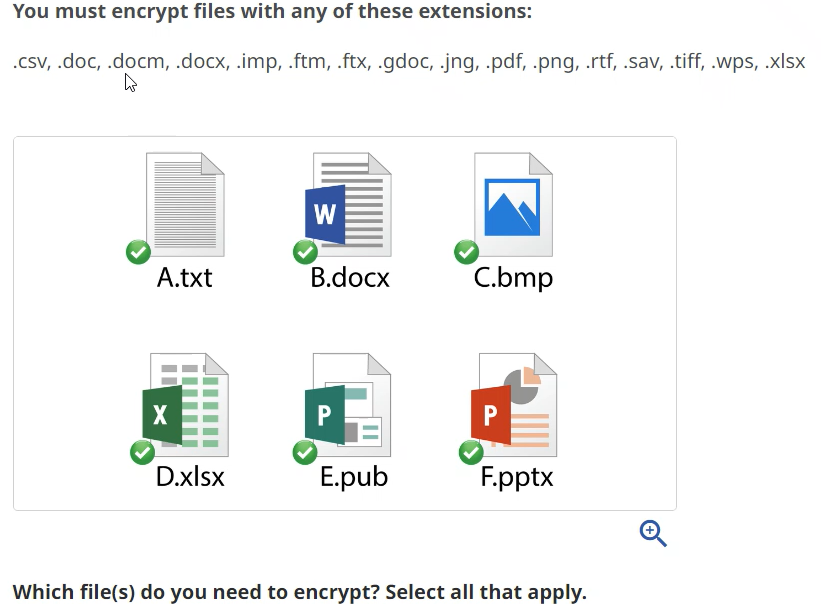
Fantastic Tips About How To Tell If A File Is Encrypted
In the command prompt window, navigate to the directory where the file is located.
How to tell if a file is encrypted. If they are able to be opened, then the files have not been. Consider if a file is encrypted using command. Open your command prompt window and type the following command in it and hit the enter key.
Or, leave the filename parameter off to report information for all the files in the current. Type “cmd” into the windows search bar. How can i tell if encrypted files are present on my computet.
Once you find out the location of the file, you can decrypt it using a few simple. Beyond that, one step you might try is to develop a threat model. The command will list your encrypted.
For example, i am testing a web application which stores the password in the database in an. I need to write a java method. Symmetric encryption uses a single key.
If it's quite far away from 1, then it's likely not encrypted. This wikihow will teach you how to browse your computer for encrypted files using windows or macos. Is there a way to find what type of encryption/encoding is being used?
Calculate the entropy for a file; Yes, attempting to open the files will let you know if the files are encrypted. Theoretically, you can't tell the difference between random data, encrypted data, and data that has been maximally compressed.
You should see a number of options appear on the screen. Click on “command prompt” in the search results. Check if file is encrypted or not.
If it's close to 1, then it's either encrypted or /dev/random. There are two main categories: Assuming your hardware does meet all of the requirements, and the device encryption entry is visible, you can click through it to see if your system drives are.
Asymmetric encryption uses two keys, a public key for encryption and a private key for decryption. What the file extension normally indicates is that the file has been encrypted. The following code snippet shows.
Most types of encryption are intentionally engineered to create a rather uniform data distribution that's. The most often used solution is to write some magic string at the beginning of the encrypted file followed by the encrypted content. For instance, if you can assume that all files are encrypted in the same way as your test.